Build powerful integrations with DoorFlow's REST API. Access control, reservations, and real-time event streaming for modern buildings.
Our DoorFlow libraries handle authentication and make integrations seamless. Clone the sample app to see a working integration in five minutes.
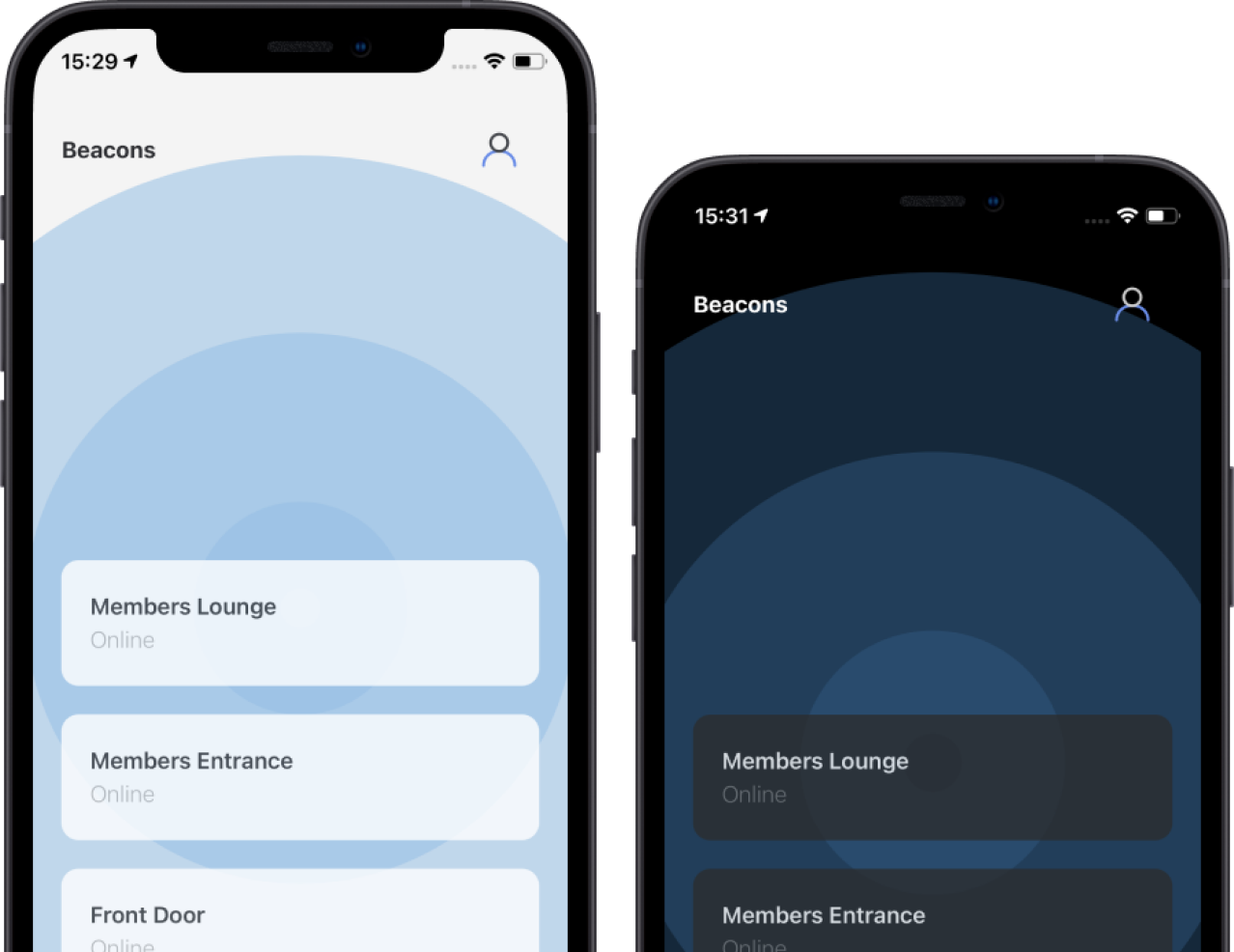

Complete reference for all DoorFlow API endpoints. Manage people, channels, access control, and reservations programmatically.
Explore endpoints
Get started in minutes with our step-by-step guide. Create your first OAuth application and make your first API call.
Start building
Step-by-step guides for OAuth setup, core concepts, common workflows, and best practices.
Browse guides
Stay up to date with the latest features, improvements, and announcements from DoorFlow.
See updates